Renewing Let’s Encrypt certificates using a systemd timer
Posted on
When deploying certificates from Let’s Encrypt, you’ll want to automate the renewal process since the certificates issued are valid for only 90 days. If you’re using Arch Linux, or another distribution that has adopted systemd, you can configure a systemd service and timer to automatically renew your certificates using the Certbot client. This approach allows you to manage the service using systemctl and journalctl, and does not require that the cron job scheduler be installed.
Before setting up a systemd service, you should run sudo certbot renew --dry-run to test your renewal configuration.
Service unit file
Service unit files contain information about a process controlled and supervised by systemd.
Create a service unit file. Service units installed by the system administrator are typically stored in /etc/systemd/system/ directory, but this may vary depending on the Linux distribution.
[Unit]
Description=Certbot Renewal
[Service]
ExecStart=/usr/bin/certbot renew --post-hook "systemctl restart httpd"The above service executes the certbot renew command and restarts the httpd service after the renewal process has completed.
Timer unit file
Timer unit files contain information about a timer controlled and supervised by systemd. By default, a service with the same name as the timer is activated.
Create a timer unit file in the same directory as the service file. The configuration below will activate the service weekly, and 300 seconds after boot-up.
[Unit]
Description=Timer for Certbot Renewal
[Timer]
OnBootSec=300
OnUnitActiveSec=1w
[Install]
WantedBy=multi-user.targetUsing systemctl and journalctl
To start the timer:
$ sudo systemctl start certbot-renewal.timerTo enable the timer to be started on boot-up:
$ sudo systemctl enable certbot-renewal.timerTo show status information for the timer:
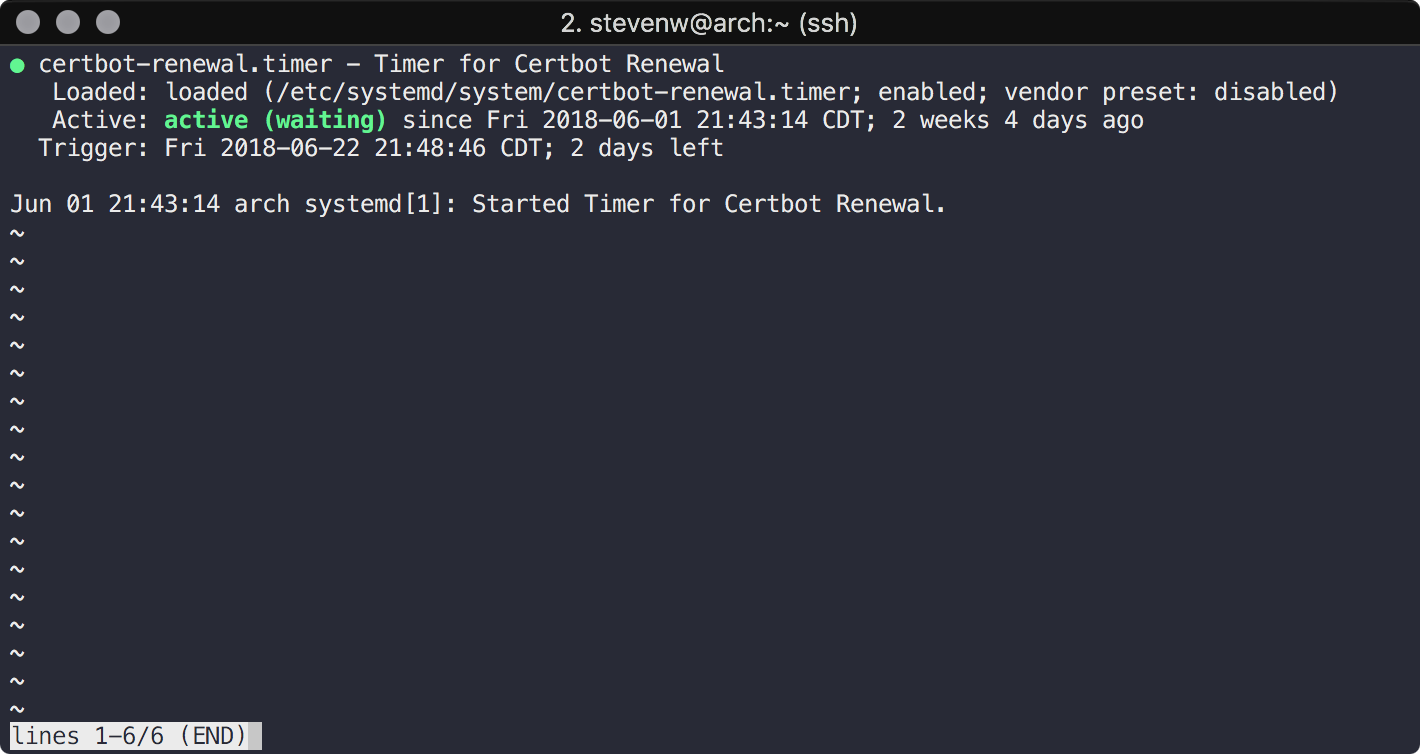
$ systemctl status certbot-renewal.timer● certbot-renewal.timer - Timer for Certbot Renewal
Loaded: loaded (/etc/systemd/system/certbot-renewal.timer; enabled; vendor preset: disabled)
Active: active (waiting) since Thu 2017-06-22 14:25:42 CDT; 5 months 8 days ago
Trigger: Thu 2017-12-07 13:36:49 CST; 6 days left
Jun 22 14:25:42 arch systemd[1]: Started Timer for Certbot Renewal.To show journal entries for the timer:
$ journalctl -u certbot-renewal.service-- Logs begin at Wed 2017-06-21 11:15:09 CDT, end at Thu 2017-11-30 12:38:26 CST. --
Jun 22 13:53:14 arch systemd[1]: Started Certbot Renewal.
Jun 22 13:53:16 arch certbot[3299]: Saving debug log to /var/log/letsencrypt/letsencrypt.log
Jun 22 13:53:16 arch certbot[3299]: Cert not yet due for renewal
Jun 22 13:53:16 arch certbot[3299]: -------------------------------------------------------------------------------
Jun 22 13:53:16 arch certbot[3299]: Processing /etc/letsencrypt/renewal/example.com.conf
Jun 22 13:53:16 arch certbot[3299]: -------------------------------------------------------------------------------
Jun 22 13:53:16 arch certbot[3299]: The following certs are not due for renewal yet:
Jun 22 13:53:16 arch certbot[3299]: /etc/letsencrypt/live/example.com/fullchain.pem (skipped)
Jun 22 13:53:16 arch certbot[3299]: No renewals were attempted.
Jun 22 13:53:16 arch certbot[3299]: No hooks were run.